vulnerabilities light: Even the BSI warns of the Flash player
A few days ago Facebook’s head of security Alex Stamos has demanded that Adobe set the Flash player should, Mozilla wants to Flash in Firefox block them entirely. This is due to the recurrence of severe vulnerabilities. The Adobe has concluded yesterday with the update to version 18.0.0.209 neuveröffentlichten indeed, yet the Federal Office for Security in Information Technology (BSI) provides a risk in the software.
Therefore, the Office has the Flash player now set to its weaknesses traffic light to red. This list is intended to show users at a glance, how safe is the use of standard software of Adobe, Microsoft, Apple, Google, Oracle and Mozilla. In addition, the Linux kernel is listed with.
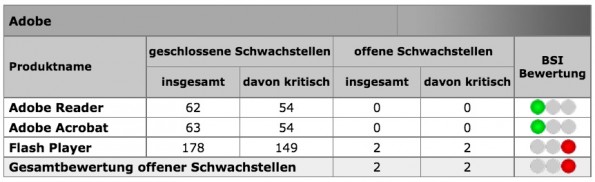
BSI vulnerabilities light: Interpretation is everything
From an obvious problem with the timeliness aside times, are the data of BSI quite in need of interpretation. The vulnerabilities light shows you initially just how many open and closed security holes in the monitored Software exist or were. In addition, this is how many of them should be regarded as critical.
It can be read, for example, that of all the monitored programs of Internet Explorer with 179 has the most closed critical vulnerabilities. However, the value in itself does not say much about the security of the browser. After all, they were stuffed – and a vendor who spends more time and money for finding security-related errors is likely to find in the long run even more of them in its software. In addition, there are often multiple versions of a software that combines the BSI in its statistics, however. More important for the user is likely to total the question be, how quickly a manufacturer on vulnerabilities and how generally dealt with it.
hanging now to our Facebook page and you secure your #Wissensvorsprung t3n like this
! >
No comments:
Post a Comment